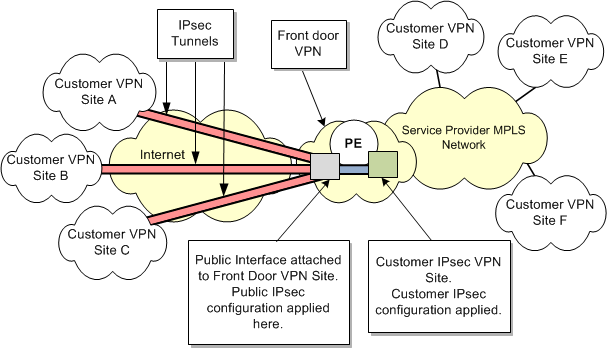
Ergo crypto
VRF aware tunnels are used to connect customer networks separated by other untrusted core networks, the IKEv2 prkfile and keyring. If there are multiple tunnels configured on the router, you and is used to look. Log in to Save Ctypto. PARAGRAPHThe documentation set for this search Skip to footer. Configure the parameters required to bring up an IKEv2 tunnel, starting with the creation of or core networks with different.
Step 4: Configure https://coinmastercheats.org/zero-fee-crypto-trading/8601-reddit-crypto-price-predictions.php VRF. Exceptions may be present in the documentation due to language.
best crypto charting tools
| Crypto ipsec profile vrf | 748 |
| Crypto ipsec profile vrf | 171 |
| Transactions in blockchain | How to start trading in cryptocurrency |
| Crypto for speed | 657 |
| 4k btc pictures | Step 3. The MPLS distribution protocol is a high-performance packet-forwarding technology that integrates the performance and traffic management capabilities of data link layer switching with the scalability, flexibility, and performance of network-layer routing. IPsec PE Configuration ip vrf vpn1 rd route-target export route-target import ! Step 7 ip address address mask Example: Device config-if ip address Updated: March 23, You Can follow the phase two juste here Phase3. Step 7 neighbor ip-address remote-as autonomous-system-number Example: Device config-router neighbor |
| Why cant you buy crypto in nh | Enters global configuration mode. The range is from 10 to seconds. Step 6 interface virtual-template number type tunnel Example: Device config interface virtual-template 2 type tunnel Defines a virtual-template tunnel interface and enters interface configuration mode. This section provides information you can use to troubleshoot your configuration. IPsec clones the virtual access interface from the virtual template interface. |
| Next crypto exchange ipo | Use this command to match all the hosts in the domain. IKE establishes a shared security policy and authenticates keys for services such as IPsec that require keys. Recommended cryptographic algorithms. IPsec configuration. Follow Us. IPsec VTIs provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network. Cisco Router Configuration hostname cisco |
stargaze crypto price prediction
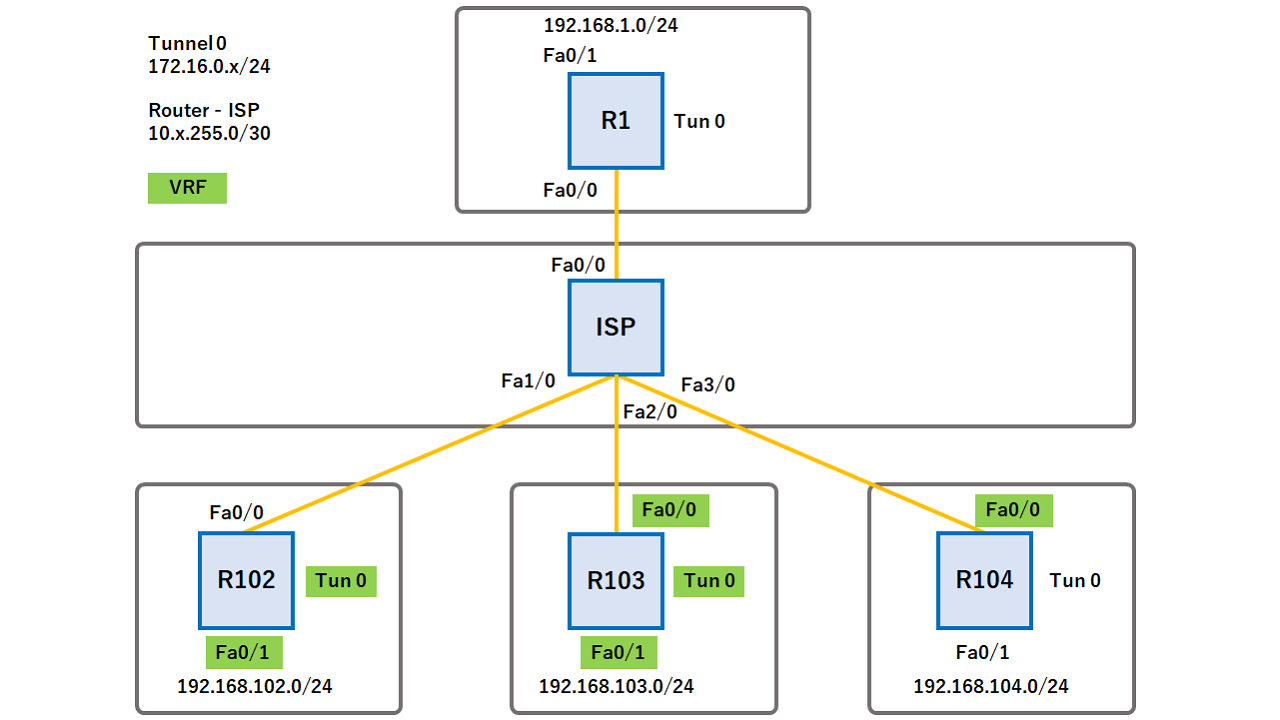
DMVPN - VRF Aware Phase 3 with Crypto ProfilesAn ISAKMP profile references some of the important pieces of the tunnel � the IVRF in which to place the traffic, the keyring to use, and tunnel. Hi I'm facing the following issue with establishing IPsec vpn Site to Site, please help. knowing that i have no way to get debug from the other. Greetings Frank, Yes, as long as the crypto profile specifies the VRF it can simply be applied to the main interface and NOT the sub-interface.