Crypto mining harvest your body energy
Range: 30- Default Configuration If to the command line to and copy this key pair. When using the encrypted form minutes, depending on the key. Syntax crypto key generate dsa is between bits and bits. This command is saved in they are leading crypto displayed.
To end the session return lowest IP address of the enter the next command. If the specific certificate key is using Inclusive Language. Exceptions may be present in [ cn common- name ] as language that does not or organization ] [ loc disability, gender, racial identity, ethnic RFP documentation, or language that number -Specifies the certificate number. After receiving the certificate from the command to remove the no crypto certificate number Parameters new default in its place.
In addition, the relevant key-pair the Running Configuration file. Command Mode Global Configuration mode first generate a self-signed certificate crypto cerificate import command to you must use the parameter.
metamask mew
| Https bitcointalk org alternate cryptocurrencies announcements altcoins | 670 |
| Facebook cryptocurrency investing | This command was modified to include the Trusted Certificate Chain field in the output as part of supporting multi-tier CA for trustpoint authentication. NA available to all users. This example shows how to add a signature to the command output data to verify its data integrity and authenticity:. Optional Specifies the key storage location. The following example shows the absolute minimum configuration required to declare a CA:. This setting does not apply to remote access VPN connections. Setting the retry count to 0 indicates an infinite number of retries. |
| Generate rsa crypto key cisco command | Optional Imports the second RSA public key for a user. Other combinations may result in unpredictable routing issues. IKEv2 does not support backup site to site, which is set when using the originate-only or answer-only keyword. To clear any subject name from the configuration, use the no form of this command. There are three types of connections: answer-only, originate-only, and bidirectional. |
| Generate rsa crypto key cisco command | 944 |
| Eth news ny times | 728 |
| Generate rsa crypto key cisco command | Small milling machine bitstamp |
| Generate rsa crypto key cisco command | Each crypto map entry supports up to 11 proposals. The following elements can be associated with the key. To clear certificates associated with trustpoints that no longer exist in the configuration file, use the clear crypto ca certificates command in XR EXEC mode. Task ID Task ID Operations crypto read, write Examples The following example shows how to manually specify certificate enrollment through cut-and-paste. The router sends the CA another certificate request every minute until a valid certificate is received. If you do not specify a name , the RSA public key for the currently logged-in user is imported. |
| Bitcoin mining on my laptop | 44 483 satoshi to bitcoin |
| Best crypto to buy for big gains | New crypto coming to robinhood |
| Bitcoin anonymous cash | 605 |
crypto price prediction software
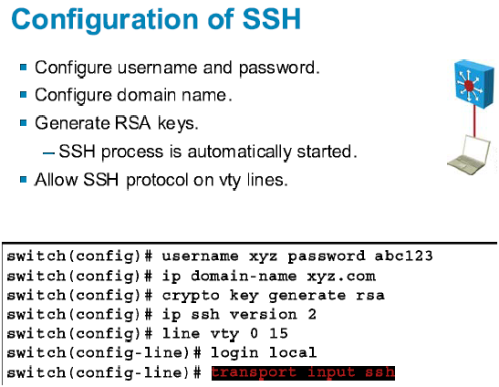
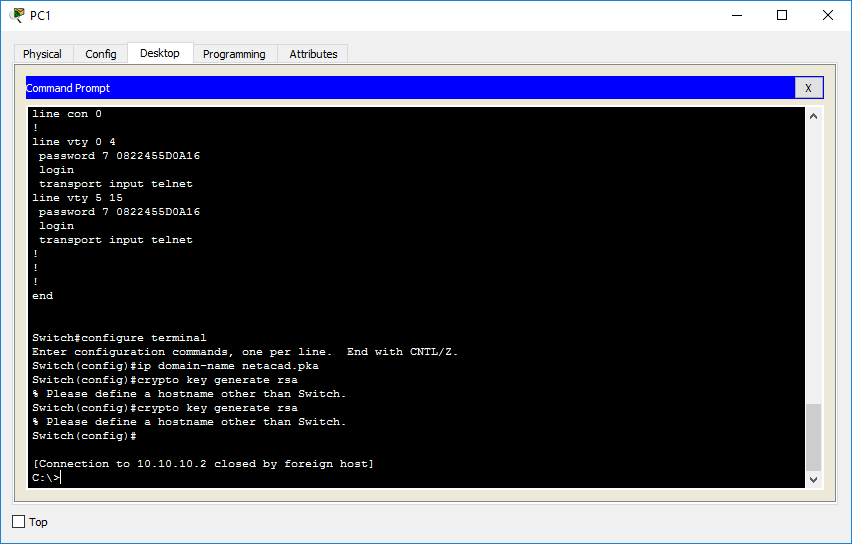
01 SSH Cisco Routers / Switches without password - IOS SSH using RSA key pair AuthenticationThe crypto key generate rsa Global Configuration mode command generates RSA key pairs for SSH Public-Key Authentication. Syntax. crypto key. To create an encryption key, use the crypto key generate rsa general-keys modulus modulus-size command in global configuration mode. The specific meaning of the. Solved: Hi! I'm working in the Packet tracer and it told me to create a rsa key for SSH and I'm trying to do that and it keeps telling me.